Cyber que puedo hacer ? Cyber que puis-je faire ? Cyber What can I do?
-
-
Questions Cyber sécurité Tentez votre chance

Course categories
Skip available courses
Available courses

- Teacher: Franck Cormary

Conocerás cómo se organiza la lucha contra la ciberdelincuencia en Francia y en Europa. La formación de los investigadores, el marco legal, las criptomonedas, la investigación de piratería informática, las estafas, la pornografía infantil. Tendremos demostraciones de los programas informáticos utilizados por los investigadores y podremos compartir algunos de ellos.
- Teacher: Franck Cormary
Dans ce cours, vous apprendrez à enregistrer un courrier électronique, à en extraire des informations techniques intéressantes, à effectuer des vérifications sur Internet à l'aide de solutions libres.
Vous pourrez vous entrainer à un jeu interactif sur la fraude au Président réalisé par le CDSE https://cdse.fr/

In this course you will learn how to save an email, extract interesting technical information from it, perform Internet checks using open source solutions.You will have an interactive experience on CEO Fraud, a CDSE production https://cdse.fr/

Cyber Security Basics & Legal Frameworks
You're CISO or you're working in IT, during an incident, a cyber attack, how do you prevent and prepare yourself?
What is the legal landscape?
Make your IOC an evidence at Court.

Program
- Legal framework
- International standards, ISO 27032/NIST SP 800-86
- Forensic approach, a triage tool
- Teacher: Franck Cormary

 ROCK PART I ONLINE INVESTIGATIONS
ROCK PART I ONLINE INVESTIGATIONS
The Regional Operational Centre in Khartoum in support of the Khartoum Process and AU-Horn of Africa Initiative (ROCK) is a regional project to fight criminal networks involved in human trafficking and smuggling, financed by the Emergency Trust Fund for Africa of the European Union, which was launched as part of the Khartoum process at the request of countries from the Horn of Africa.
To combat these illicit activities, the ROCK promotes the exchange of information and expertise that is essential in the fight against these criminal networks, while paying particular attention to strengthen the criminal justice chain and to enhance the prevention to protect victims.
Sharing information on irregular migration and associated criminal networks along migratory routes, as well as creating the conditions for their operational use in a legal and judicial framework, is a prerequisite to address transnational crime of THB and SoM.
Social media has been used by traffickers to recruit victims, to proliferate their trafficking operations (mainly for sexual exploitation) and to control victims through restricting their social media access, impersonating the victim, or spreading lies and rumors online. The internet has revolutionized human trafficking and this falls within the scope of ROCK.
- Teacher: Franck Cormary

 ROCK PART II UNDERCOVER ONLINE INVESTIGATIONS
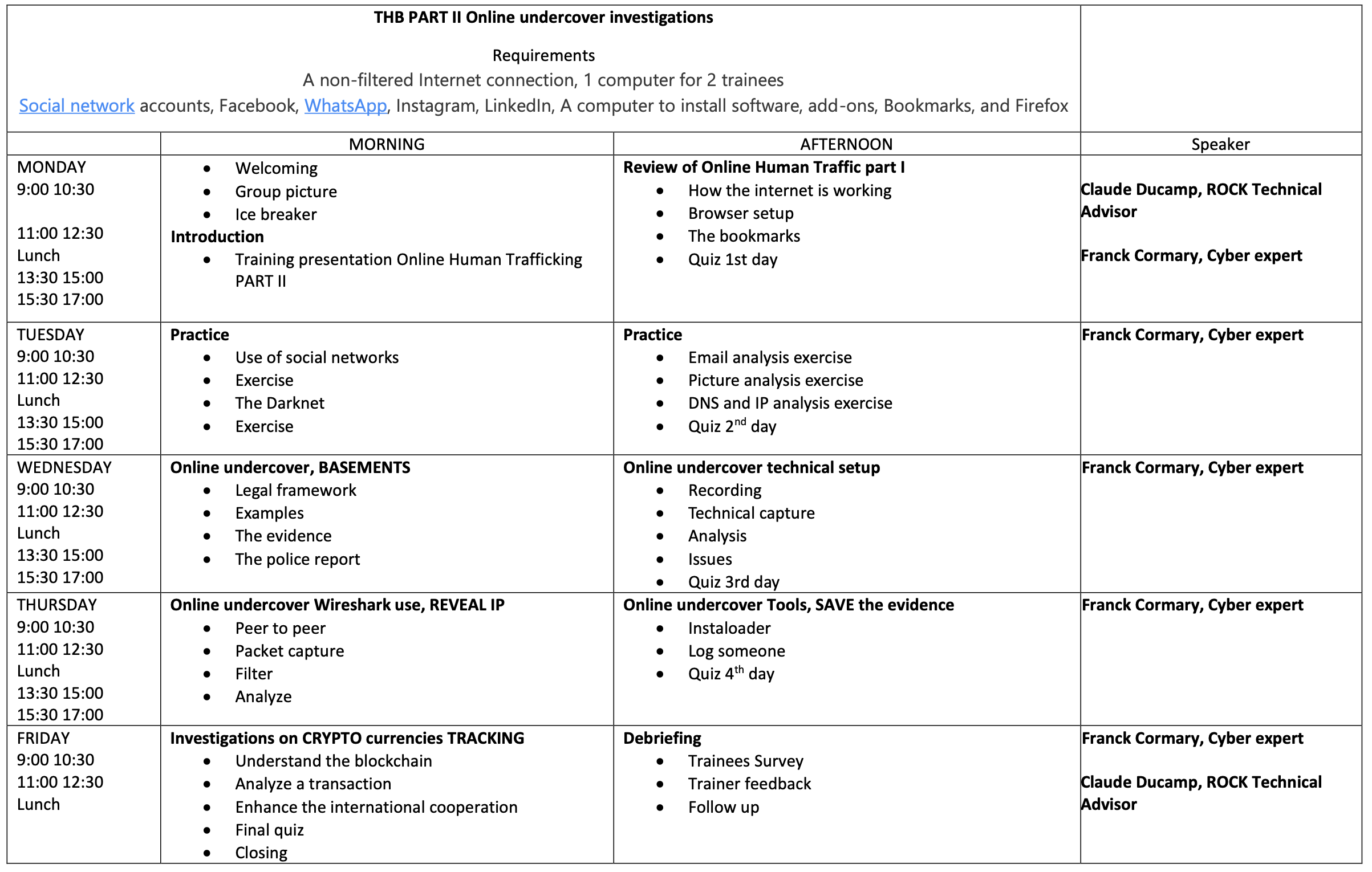
ROCK PART II UNDERCOVER ONLINE INVESTIGATIONS
This course will enable you to improve your knowledge of online investigations.
- Prepare and use your technical equipment
- Collecting and analyzing data
- How to be undercover online
- Using tools to identify people
- Examining crypto-currencies
- Test your knowledge

This general evaluation on computer science will open you the doors of the others training
- Teacher: Franck Cormary

This course aims to prepare a cyber forensic first responder training.
- Teacher: Franck Cormary

- Teacher: Franck Cormary

You will learn what all the detectives must know,
how to search Internet,
how to use tools to track people,
how to save evidences.
- Teacher: Franck Cormary

You will attend theory and practice course on forensic examination from a bootable USB stick called DARWIN
This tool is used in France by First Responders to get an overview of the suspected computers and prioritize the technical searches
The visited computer is write protected to be compliant with the chain of custody
The E-learning training will prepare you for the face to face training
- Teacher: Franck Cormary
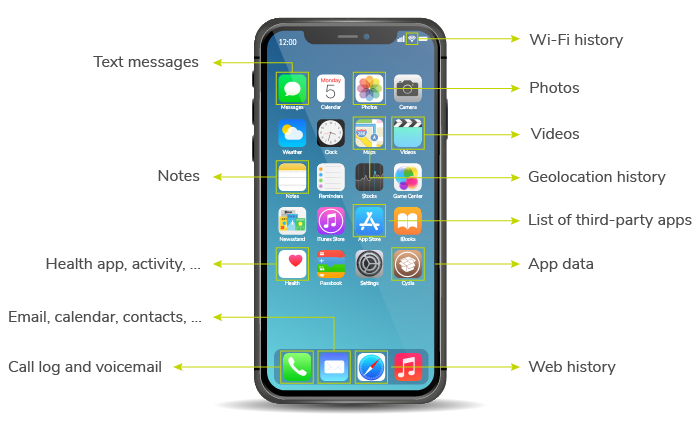
This training is 9 modules to be able to understand how to seize, extract analyze and share DATA from a mobile device
- Introduction to mobile devices
- Precautions
- Phone detective
- Different kind of extractions
- Root and Jailbreak
- UFED 4 PC
- IOS extraction
- UFED Physical analyzer
- UFED reader
- Teacher: Franck Cormary

- Teacher: Franck Cormary

program: The trainees will have to know the different functionalities of the online training platform MOODLE. Thus they will be able to carry out various actions of maintenance, promotion, creation and management of contents.
1. General presentation of the management interface of the Moodle site
2. Management of the user database, maintenance and verification of the database
3. Creating "cohorts" for easier user management
4. The different roles and rights within the interface management, Admin, Manager, Teacher, non editing teacher, trainee
5. Creation of new users, manual, in groups from a list, inclusion of users in "cohorts
6. Management and filtering of users
7. Manage the presentation of courses on the Moodle, create categories
8. Course management
9. Enrolment of students in courses, individually, by "cohorts
10. Creation of groups within a course
11. Strategies and rules for Moodle administration by the training department
- Teacher: Franck Cormary